The 2023 Imperva Bad Bot Report: APIs under attack

|
Getting your Trinity Audio player ready...
|
• The 2023 Imperva Bad Bot Report explains the new danger to APIs.
• Bots are the perfect predator programs for APIs.
• Bots can drain cash from businesses.
In Part 1 of this article, we sat down with Peter Klimek, Director of Technology, Officer of the CTO at Imperva, to talk through the headline of the 2023 Imperva Bad Bot Report – the increasing use of bad bots both by bad actors to hijack online purchases and raise the re-sale prices through the roof, and by what are technically good actors (civilians who’ve been denied access to the products they want by bots), who themselves are now resorting to using bad bots to out-bot the bots.
But the Imperva 2023 Bad Bot Report is a relative treasure trove of data about what bots are upto these days – and some of them are doing more than cheating the line for Taylor Swift tickets.
While cheating fans out of the chance to see the millennial Dolly Parton is bad enough, where the rise of the bad bots gets particularly serious is when they start interfering with APIs.
APIs are application programing interfaces – they’re the way two or more computer programs talk to one another, and they very much hold business systems together in the 21st century.
Letting bad bots play with APIs – bad news, we’re guessing. While we had Peter in the chair, it seemed like the ideal opportunity to get very, very depressed.
THQ:
This year’s Imperva Bad Bot Report records an increase in bot attacks on APIs. Because of course it does. Are APIs just especially vulnerable? Or are the bots getting more sophisticated?
The Imperva Bad Bot Report – why APIs?
PK:
Yeah, this was one of the really big themes in this year’s Imperva Bad Bot Report. Bad bots are effectively coming for API’s. There are a few reasons for that.
First and foremost, the sheer volume of API traffic has increased substantially. Organizations in the last five years or so, and in particular within the last couple of years, have gone through modernization programs. Many of them moved workloads to the cloud, many of them started offering new services.
And really, if you look at how those applications are built, in many instances, they’re exposing public APIs. So that’s a big driver behind the rise in bot attacks.
Now, APIs themselves are also very attractive targets for bots. APIs, by definition and by design, are machine-readable. They’re designed for machine-to-machine traffic. And so if you’re a bot operator, and you have the choice of whether to write clunky scripts that have to go and crawl and scrape a website and load all those resources, or to just go to the source and take the actual data from where it’s all in a format that’s easy to parse, easy to iterate and easy to read through, you’re going to take that second option.
Also, a lot of organizations build these APIs because they’re powering their single-page web applications, or their mobile applications. And they think that just because it’s only being used by their mobile application, that it’s not going to be discovered by a bot operator, and that a bot operator is not going to go and target them.
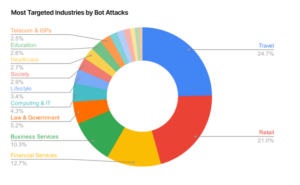
A breakdown of bot attack by industry from the Imperva Bad Bot Report.
THQ:
You’re going to tell us they’re monstrously wrong, aren’t you?
PK:
Hence the rise in attacks on APIs. APIs as a whole have been something of a blind spot for a lot of enterprises, because frankly, for most security teams, they don’t know what’s actually in their APIs. They don’t know what they’re doing. And it can be really hard to get into that level of detail without going and talking to the developers.
THQ:
So a) companies and teams don’t know they’re vulnerable, and b) when they discover they’re vulnerable, there’s not a lot they can do about it without going back to the developer?
It sounds like one of the reasons that bot attacks on APIs are going up is that they’re practically the perfect victim for those particular malicious programs.
PK:
Yeah, that’s it exactly. It’s a very natural evolution. But ultimately, it’s a security gap that exists today. Part of the reason we highlighted this so heavily in this year’s Imperva Bad Bot Report was just to showcase and educate our customers that they’re probably not thinking about this as something they need to be focused on. But it’s probably costing them money right now.
The Imperva Bad Bot Report – you’re probably going to be hit.
THQ:
Is that your message to companies on API vulnerability? It’s probably happening, you may not know about it, it’s probably costing you money?
PK:
Yeah. I’d say for companies that have this vulnerability in particular, you need specialized software to be able to detect the problem. There’s just no way that you can do this with some traditional tools that you might use.
At Imperva, we’re known for web application firewalls. But web application firewalls are not equipped to deal with sophisticated attacks. You need specialized tools to be able to deal with bot attacks on your APIs.
APIs are especially vulnerable to bots.
And ultimately, in terms of some of the specific lines of business that you have, we often see customers going in, embedding some of the detection mechanisms down into the mobile applications themselves, to better understand whether they’re dealing with a legitimate mobile device or a bot operator in there.
So I think in the first instance, just awareness of the problem is a bigger challenge than companies might imagine. Then there’s the realization that it requires special tools to deal with.
And then you’re going to have to work with various business teams, because there’s not really a one-size-fits-all solution for how you deal with the problem, it tends to be very specific to the business logic of your applications themselves.
THQ:
It sounds like having a rat infestation. You’re not aware of it to start with, big things don’t go missing immediately. But over time, you start to see the tell-tale signs.
PK:
Yes, absolutely. Most people don’t start thinking about it until they see the evidence, until there’s something that draws them to the idea that there’s a problem there.
But a lot of times, that evidence can hide.

Bots, like rats, are always nibbling – in this case at your APIs.
THQ:
Of course it can.
PK:
It’s not always that bots overzealously go and attack your site, and you have an outage as a result of it. You might just incur a 20% extra charge in terms of the amount of bandwidth that you’re serving.
Unless you’re a) looking for any extra charges, and b) can track the extra back to its source… how would you know?
THQ:
Is it worth businesses assuming that they will have a bot problem at some point? Is it worth preparing and budgeting for that?
PK:
For certain lines of business, absolutely. This is one of the big things we find – there are certain sectors of the industry that will be targeted much more heavily by bots. And the types of attacks themselves will also vary depending on the industry.
If you’re in retail ecommerce, absolutely, expect that you’re going to get scraped. Expect that there will be instances where it’s not just going to be traditional bad actors that are looking for items – sometimes it’s your competitors that are scraping you, looking for price information because they want to try to undercut you.
That absolutely that should be expected. It should go into the threat models of businesses as they’re building out new services.
Travel is another really big example. Again, we have flight APIs, and all the different services, the aggregators that are going out and providing us with the best prices.
In many cases for these travel sites, they have to pay for access to those APIs. So when bots are hitting your sites, it’s costing you money.
Within finance, in particular, we see account takeover attacks, or credential stuffing, where people are effectively reusing credentials to try to gain access to accounts. That’s a pretty common occurrence. And that applies across most industries, but especially where there’s some sort of financial reward at stake.
The Imperva Bad Bot Report – why us?
THQ:
What is it about things like travel, retail, and finance that make them particularly attractive targets for bots? Is it anything more complex than high usage and the potential for high reward?
PK:
No, those are really the core drivers for it. Everyone’s going to have to deal with a problem, whether it’s just vulnerability scanning, or DDoS attacks or things like that, that are effectively conducted by bots.
If you have the ability to accept a credit card, your system might deal with bots. What happens? Bad bots go and use that site and the ability to enter in a very low dollar amount like a single dollar and test to see if those credit cards are valid. And then the business has to deal with chargebacks and all the other kinds of fees that come along with those.
So there are a whole lot of different use cases for it. And I think that’s what really makes the space so interesting is that not every problem is the same. And it’s always going to be very business-specific.
THQ:
That seems to be the hallmark of bots. They’re not too big and flashy, and they’re not going to ruin your day in a hurry, like ransomware. They just sit there. Nibbling. Always, always nibbling.
PK:
Yep, absolutely. I love your analogy about bots being like an infestation of rats. You might not notice one, or you might make your peace with the idea that one’ll be there.
But all of a sudden, you haven’t got one. You’ve got ten – and then you’ve got a problem on your hands.
In Part 3 of this article, we’ll talk bots and generative AI, and see what impact the new technology has on the bot landscape.










