Could cl0p’s MOVEit supply chain attack become a new normal?

• The MOVEit supply chain attack hit over 130 organizations worldwide.
• Distinct from ransomware, it advised affected companies to negotiate with the hackers.
• Could the hugely successful attack inspire others?
On June 8, 2023, we reported the beginnings of what could well become a record-breaking supply chain attack by the cybercrime group with the stupid name – cl0p.
The organization, rather than delivering a single, massive ransomware attack, with all the administration and tedium that can sometimes involve, went about its business in a rather more chaos-friendly manner. It pulled off – and then stayed silent about – a highly significant supply chain attack on the MOVEit software.
That software, used in the Zellis payroll system among others, had a fairly simple role in life – it existed to facilitate what it now feels massively ironic to describe as secure file-sharing.
By the time news of the attack broke, several significant targets had been identified – particularly in the UK to begin with. The recently much-troubled BBC, the UK’s national broadcaster of record, was hit. So too was the UK’s “national airline,” British Airways, along with the Boots pharmacy chain, which has over 2,200 branches across the country.
Supply chain attack goes viral.
But it was immediately clear that the supply chain attack was going to be potentially much bigger than three high-profile UK-based targets.
As is often the case with supply chain attacks, even cl0p itself wasn’t entirely sure how far the extent of its success would run. That’s why, for instance, it issued no ransoms for the data it had amassed through infiltrating the MOVEit software.
There was so much of that data, it made more sense to simply let every organization that might have used the software within a given space of time know that their data might be among that which had been hacked, and encourage those organizations to get in touch with the hackers to negotiate what they thought was a suitable price not to have the data dumped like chum in the shark-infested waters of the dark web for anyone with a grudge or a get-rich-quick scheme to use.
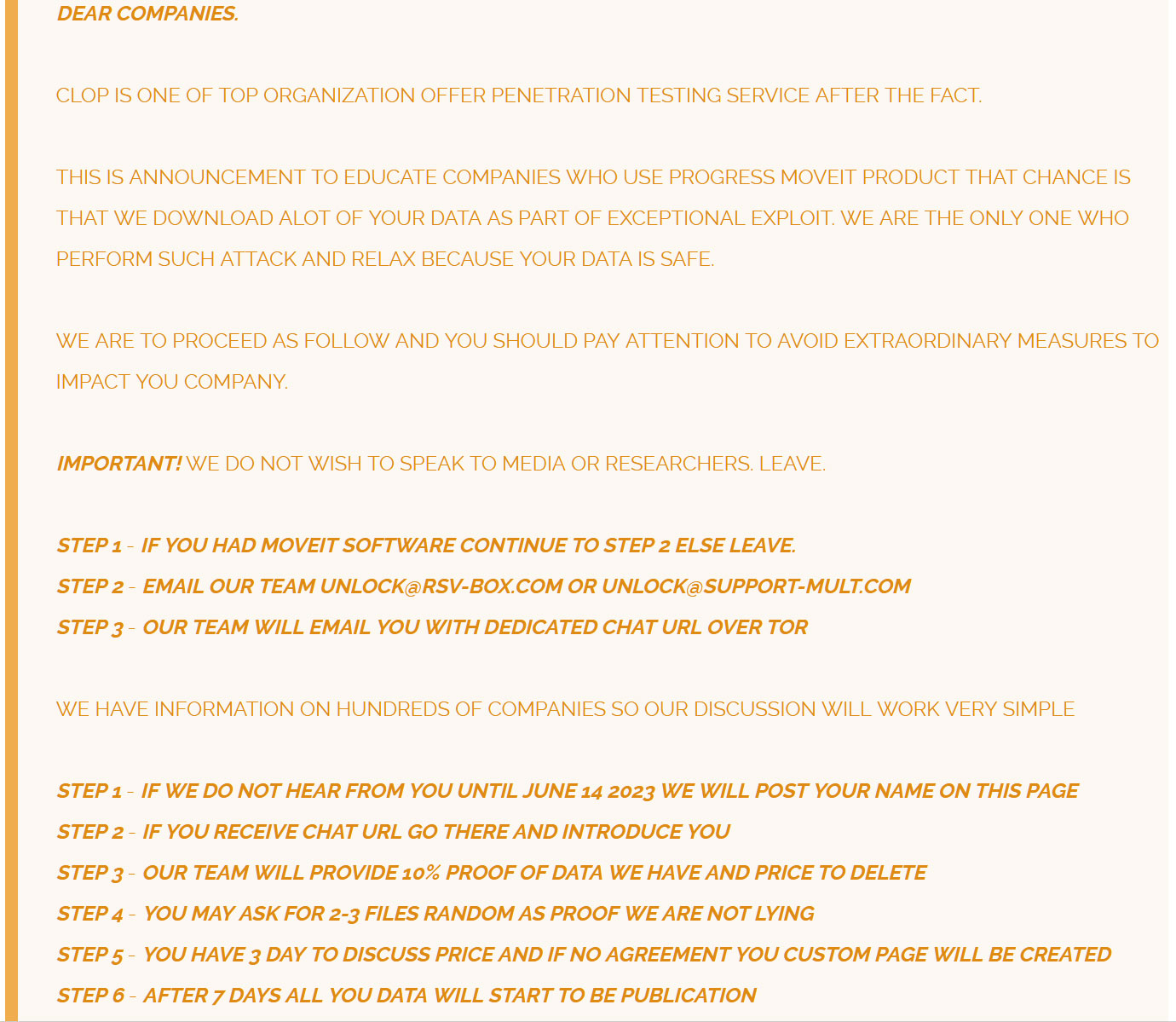
Instructions, rather than ransoms, for the cl0p supply chain attack.
As of July 6, the supply chain attack was confirmed to have affected data belonging to at least 15 million individuals across 130 companies worldwide, including the likes of Shell, Siemens Energy, Schneider Electric, UCLA, Sony, EY, Aer Lingus, PwC, Cognizant, and AbbVie, as well as law firms, Kirkland & Ellis and K&L Gates.

When a supply chain hack hits major companies like Shell, it’s big news.
The attack continued to grow in scope, with universities and student organizations confirming they’d been hit, from the University of Georgia (UGA), New York City Department of Education, and University System of Georgia (USG) to UnitedHealthcare Student Resources (UHSR), and Landal Greenparks.
And then, like ripples on a lake but nothing like so organized, it started affecting whole state governments and large networks, including the State of Missouri, the State of Illinois, the government of Novia Scotia, the American Board of Internal Medicine and Ireland’s Health and Safety Executive.
The US government versus supply chain attacks.
When it became clear that cl0p had captured data from US federal agencies, most notably the Department of Energy, the State Department stepped in, putting US$10 million on the table for anyone who could provide information that linked cl0p to a foreign government via its Rewards For Justice program.
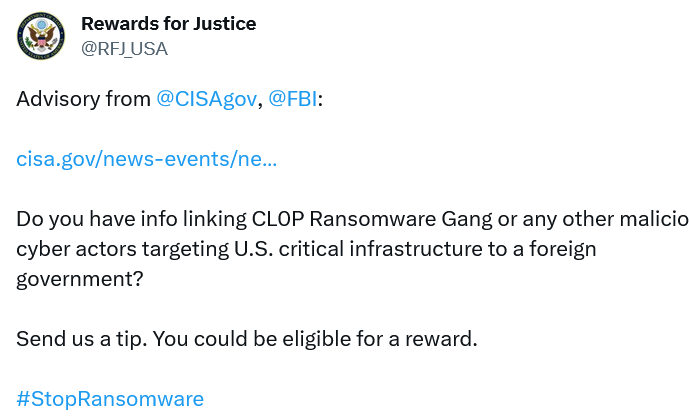
Rewards for Justice – like the Justice League… but with bribes.
It remains as yet unclear quite how many victims have been affected by the cl0p supply chain attack, or how many have paid how much to stop their data appearing on the dark web.
Certainly though, cl0p has started releasing that collected data into the world – presumably from some among the many organizations that will have been advised not to pay a cent to the hackers.
But the known scale of the attack makes it likely to be one of the major data heists of recent, if not of all times, and it highlights the rise and rise of the supply chain attack as, if anything, a significantly worse headache even than targeted malware or ransomware.
The stealthy, effective theft of large swathes of data through a commonly used and previously trusted program, coupled with the almost anarchistic acceptance of chaotic results by the cybercriminals breaks down any sense of “the game” of cybercrime as it has traditionally been played on a more one-to-one basis in the past.
It’s also worth noting that Progress Software patched the MOVEit program as soon as it became aware of the intrusion by cl0p – but sadly by that point, enough damage had been done to facilitate this blockbuster movie-scale supply chain attack.
The vast attack surface of a supply chain.
We spoke to Bernard Montel, technical director of cyber-firm Tenable about the impact of the attack.
“Vulnerabilities are disclosed every day, with threat actors poised and ready to see if they can monetize the flaw. There are two elements to be considered when any new vulnerability is revealed – how complicated would it be for threat actors to use the flaw, and what is the likelihood that it will be exploited?
“The latter typically comes down to the level of adoption of the affected software – the more prevalent it is, the higher the likelihood of exploitation.
“This latest flaw revealed by Progress Software is the perfect storm. An unauthenticated SQL injection flaw is easily exploited by threat actors with little technical know-how, providing bad actors with a number of options – from adding a field to a webpage to steal information from unsuspecting users filling in the ‘form,’ to tricking the application with an ‘sql query’ to disclose all the information in any back-end database. In this case the door is fully open for bad people to enter without being challenged.
“Instead of waiting to be attacked and then responding, it’s vital that security teams take a preventive approach to cyber-defence. The need to understand your attack surface and proactively manage risk to the business has never been more urgent.”
At the time of writing, it remains entirely possible that more victims of the MOVEit supply chain attack will be identified, and certainly the future of the stolen data remains uncertain.
But the effectiveness of the MOVEit supply chain attack suggests that it may usher in a new era, where such attacks are increasingly common – so managing the risk of your attack surface may become increasingly crucial in the next five years.











