Kaspersky: North Korean state-sponsored hackers behind the Maui ransomware attacks

- The attacks involved modifications of the well-known malware, DTrack, as well as the use of the brand-new Maui ransomware.
- Kaspersky’s assessment shows that the actor is opportunistic and may compromise any company around the world regardless of their category of business.
- Throughout this year, the group continued expanding its malware arsenal and the geography of its attacks.
In July this year, the US Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA) and the Department of the Treasury (Treasury) issued a warning to healthcare organizations around the country on the possibility of being under threat of attacks from North Korean state-sponsored actors. At that time, the hacking group Andariel had been employing a never-before-seen Maui ransomware against US healthcare organizations since April 2021.
A recent finding by Kaspersky revealed that Andariel, an advanced persistent threat (APT) subgroup of Lazarus that has been in operation for over a decade, has continued expanding its malware arsenal and the geography of its attacks throughout this year. That means the attacks were not specifically targeting US healthcare organizations alone, as reported by CISA in July 2022.
In fact, Kaspersky found that they targeted high-profile organizations even in Japan, India, Vietnam and Russia. Kaspersky’s security expert Kurt Baumgartner also noted that they have been tracking the Andariel APT group for years, and noticed that their attacks are “constantly evolving.” He also emphasized that the group has started deploying ransomware on a global scale, demonstrating ongoing financial motivations and interest, and that requires special attention.
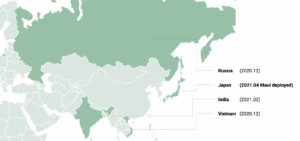
Kaspersky found that they targeted high-profile organizations even in Japan, India, Vietnam and Russia.
Source: Kaspersky
Kaspersky researchers have assessed that the actor is opportunistic and may compromise any company around the world, regardless of their category of business, instead focusing on their good financial standing.
The birth of Maui ransomware using Andariel tools
The Andariel group’s primary tool is the long-established malware, DTrack, according to the Kaspersky Threat Attribution Engine, and it was created by the Lazarus Group. It collects information about a victim and sends it to a remote host. Among other things, DTrack collects browser history and saves it to a separate file. The variant used in Andariel attacks is able not only to send the harvested information to the cybercriminals’ server via HTTP, but to store it on a remote host in the victim’s network.
When the attackers find noteworthy data, Maui ransomware comes into play. It’s generally detected on attacked hosts 10 hours after DTrack malware activation. A separate report by Stairwell concluded that the ransomware is controlled manually by the operators — that is, they specify which data to encrypt. Stairwell indicated that it has some unique characteristics that set it apart from other ransomware-as-a-service (RaaS) threats currently in play.
“That includes the lack of a ransom note to provide recovery instructions or automated means of transmitting encryption keys to attackers,” Stairwell’s principal reverse engineer Silas Cutler wrote in the report. Another characteristic of Maui that diverges from other ransomware is that it appears to be designed for manual execution by a threat actor, allowing its operators to “specify which files to encrypt when executing it and then exfiltrate the resulting runtime artifacts,” Cutler wrote.
Andariel’s have had several other significant trysts with ransomware as a means to reap monetary gains for the sanctions-hit nation. In June 2021, a South Korean entity was revealed to have been infected by file-encrypting malware following an elaborate multi-stage infection procedure that commenced with a weaponized Word document. Last month, Microsoft disclosed that an emerging threat cluster associated with Andariel has been using a ransomware strain known as H0lyGh0st in cyberattacks targeting small businesses since September 2021.










