Warning: You’re entering a bad website!
Most devices used in a corporate setting should have installed sufficient endpoint security solutions that not only protect users, but also warns them whenever they are entering a “bad website” — a potentially harmful site. But what happens when the trusted security system accidentally blacklists websites that are not supposedly “bad”? Do users still continue to access the website despite the warning signs, or avoid it altogether?
Bad websites may not just refer to poor content on the site, but can also refer to sites that have malicious, potentially damaging content. Cybercriminals will normally create bad websites that look almost as good as an original website. This way, many users are easily conned when accessing such sites. And when entering their details in said platform, which cybercriminals can then use to wreak more havoc on them.
Safe browsing continues to be advocated by internet browsers. In fact, Check Point Research (CPR) spotted over 5300 different malicious websites per week, a 178% increase compared to 2021 so far. CPR also highlighted that 1 out of 38 corporate networks are being impacted on average per week in November 2021.
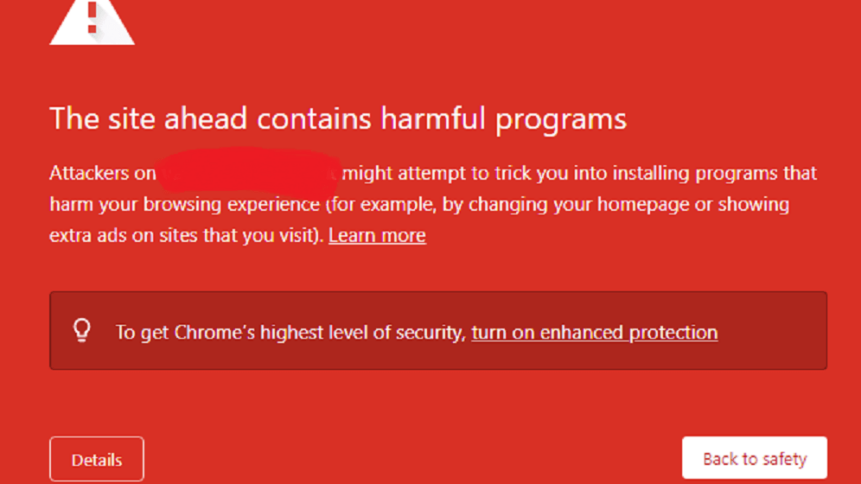
For this very reason, cybersecurity solutions that offer endpoint security like firewalls, browser protection and such often have blockers that deny access to bad websites or links that may have been compromised by cybercriminals. For example, a listing in the McAfee Blacklist indicates that an IP address or the domain of a particular website has been identified as potentially malicious by McAfee/Intel Security.
Another example is Sophos Endpoint Security and Control that detects malware on websites. It blocks access to it and displays a warning message that the site is restricted, and files may contain malicious code. Normally, the firewall would indicate which category the site has been classified as, as well as the threat source URL.
But what happens if an employee needs to access a site that has been marked unsafe for work purposes? Do they disable the firewall and proceed or do they contact their IT team to get advice on whether they can proceed to enter the site?
Today, with digital sites and virtual events being essential to remote and hybrid work, accessing third-party websites from corporate devices is a necessity. However, employees still need to be vigilant and practice safe and smart browsing when doing such.
Accessing “bad websites”
The problem with security companies blacklisting websites can be an annoying stumbling block for some organizations. Many organizations often feel that their websites have been wrongly blacklisted, leading to them losing site visits.
But it’s not all doom and gloom when a website is blacklisted. Google flags thousands of websites each day. Companies can however get their website’s security reviewed and whitelisted again. The same works with sites that have been blacklisted by security firewalls like McAfee and Norton.
Despite this, some websites take time to be whitelisted and employees need to access them for work purposes. The reality is though, if a site has been flagged, employees should never attempt to access it or disable their firewall without getting consent from their IT security teams. Failure to do so could lead to not only the employee being compromised but the company as well.
Yet, some feel it is safe to access a website despite it being flagged as there are other network security and endpoint security solutions that can protect an employee. This is not entirely true. These protection protocols are there for a reason, as highlighted by a recent virtual event that TechHQ was invited to attend, ironically by a cybersecurity vendor.
The event was hosted on a third-party site. Upon trying to access the site, security warnings were triggered as the website was flagged to be unsafe. Surprisingly, the organizers not only requested us to disable the firewall and access their platform, but also disable ad-blocking software and disconnect the VPN, which is a big breach in company security protocol.
It’s incidents like these that can lead to a company being breached. While the site may seem harmless, the moment the firewall and VPN are disabled, a device is also open to attacks from other websites and content too.
At the end of the day, bad websites exist. While endpoint security solutions flag them, these websites can still get themselves unflagged. However, if an employee’s device is breached, it can become a different scenario.
So the next time the browser warns you about a website, you might just want to double-check on a website blacklist checker or with your IT team before proceeding.










