Microsoft: More than half of state-backed hacks are by Russia

- 58% of government-linked hacks were attempts by Russia, followed by 23% from North Korea, 11% from Iran, and 8% from China
- Microsoft’s head of Digital Security said nation-state hacking has about a 10 to 20% success rate
In 2020, hacking groups from Russia targeted some three percent of the government organizations around the world. In less than a year, the number increased drastically, according to Microsoft, as Moscow-sponsored hacks were found responsible for over half (58%) of all nation-state-backed cyberattacks as of June 2021.
Concurrently, the success rate of government and non-government hacks by Russia has gone from 21% to 32% year over year, the technology giant said in a report focusing on state-backed and cybercriminal activity.
“The last year has been marked by significant historic geopolitical events and unforeseen challenges that have changed the way organizations approach daily operations. During this time, nation-state actors have largely maintained their operations at a consistent pace while creating new tactics and techniques to evade detection and increase the scale of their attacks,” the report noted.
The Microsoft Threat Intelligence Center (MSTIC) and the Digital Security Unit (DSU) have also observed that most nation-state actors continue to focus operations and attacks on government agencies, intergovernmental organizations (IGOs), nongovernmental organizations (NGOs), and think tanks for traditional espionage or surveillance objectives.
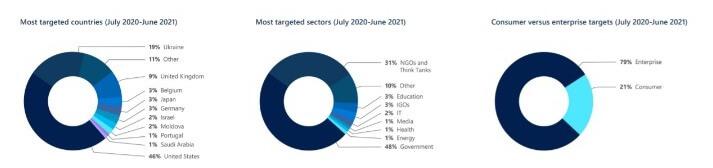
The “Most targeted sectors” chart in this chapter section shows that nearly 80% of those targeted were either in government, NGOs, or think tanks. Source: Microsoft’s report
“The victims of attacks often have information relevant to an adversary government’s intelligence needs, which is why so many government agencies and think tanks are attacked,” it added.
Prominent targets reportedly included government agencies and think tanks in the US, UK, Ukraine, as well as European Nato members. The data also includes the Russian espionage operation that breached at least nine US federal agencies in 2020 by exploiting software made by SolarWinds, a Texas-based firm.
The other usual suspects — North Korea, Iran and China
In the report, Microsoft said that while 58% of government-linked hacking attempts originated in Russia, it is followed by 23% from North Korea, 11% from Iran, and 8% from China. Of course, Microsoft did not report on US intelligence agencies, which also conduct cyber-espionage campaigns.
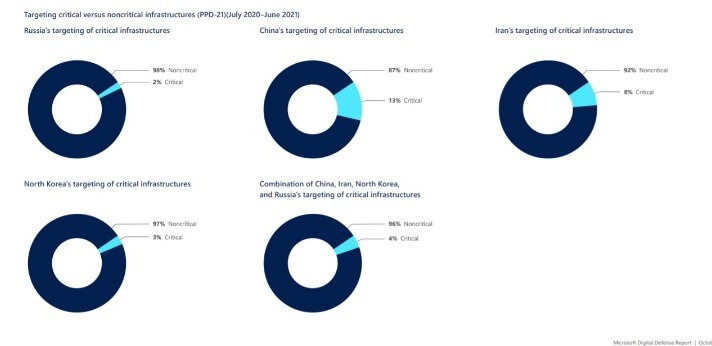
Targeting critical versus noncritical infrastructures (PPD-21)(July 2020–June 2021) Source: Microsoft
Although China accounted for fewer than one in 10 of the state-backed hacking attempts detected, the country was however successful 44% of the time in breaking into targeted networks, Microsoft said in the report.
Type of Russia hacks and other attacks
The 2020 Microsoft Digital Defense Report also identified common aims (espionage, disruption/destruction) and common techniques (reconnaissance, credential harvesting, malware, and virtual private network (VPN) exploits) prevalent among major nation-state cyber actors.
“These aims and techniques were as prevalent this year as the year before. Tried-and-true methods such as large-scale spear-phishing campaigns were still valuable tools in the kits of hackers,” it said. Microsoft also said the two main goals of nation-state actors have not changed either. In fact, in the last year, espionage, and more specifically, intelligence collection, has been a far more common goal than destructive attacks.
Microsoft concluded the report with few suggestions to improve security posture including doing the basics well, which means good cyber hygiene and implementation of basic security measures; taking a holistic view; accepting that any element can be used as an attack vector; people as key line of defense; and embracing zero trust is an architectural principle.









