Massive MongoDB database leak a data security ‘wakeup call’

Another unsecured database has been discovered on MongoDB, the widely-used open source database management system.
The discovery was made by cybersecurity researcher Bob Diachenko who identified an unprotected and publicly-indexed MongoDB database which contained more 275,265,298 records of personally identifiable information (PII) on Indian citizens.
The highly-sensitive information available publicly included attributes such as name, email, date of birth, mobile number, education, gender, as well as current employment and history, and salary (see image below).
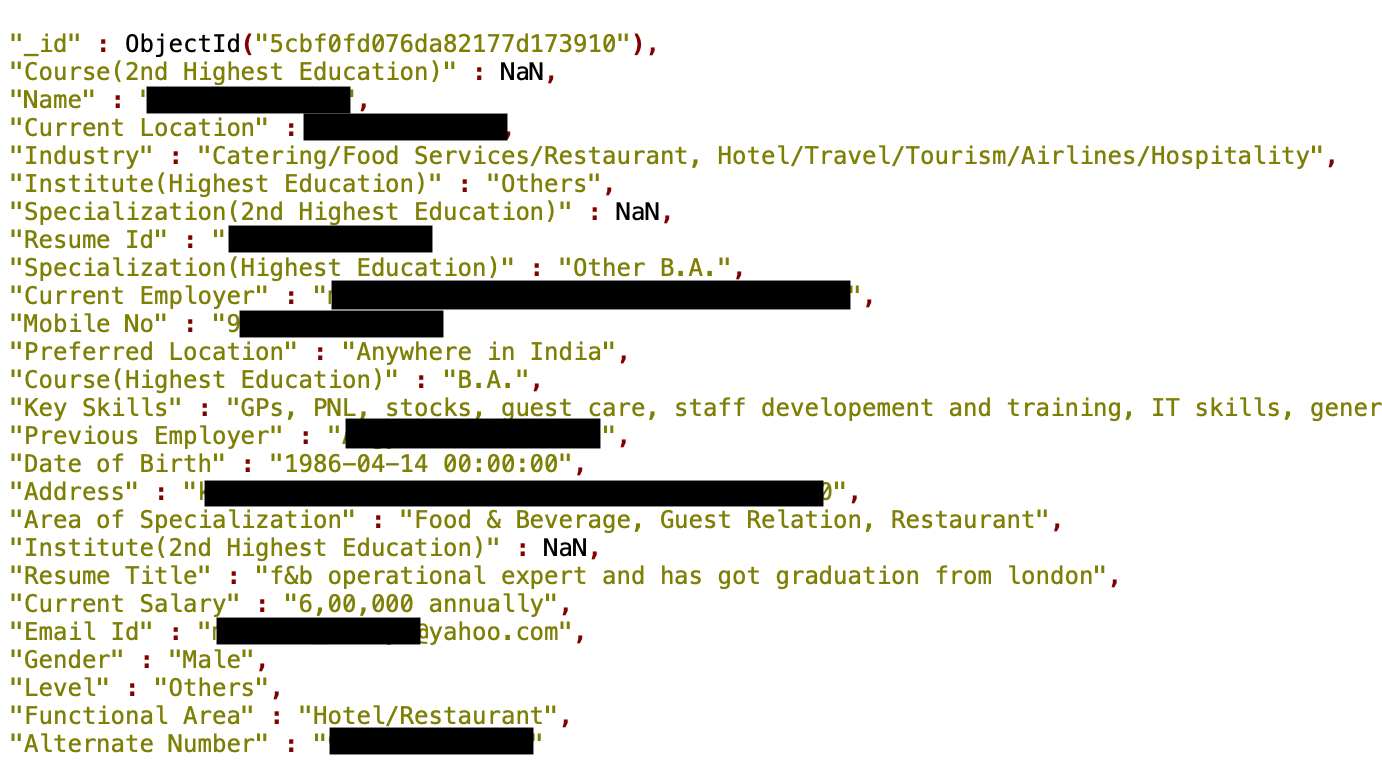
A screenshot of an individual’s PII, which was publicly available to view in the database. Source: Security Discovery
According to Diachenko, this information was hosted and publicly available for more than two weeks. The database was hosted by AWS using Shoda, with historic data showing that the PII data cache was first indexed on April 23, 2019.
There was no indication in the database as to the owner of the data or affiliation tags, but it’s likely to be collected by an anonymous person or organization as part of a “massive scraping operation”, he said.
Diachenko reported the discovery straight away to Indian CERT (Computer Emergency Response Team), but said the database had been open and searchable until May 8, when it got “dropped” by hackers pertaining to be a group called ‘Unistellar’ (see image below).
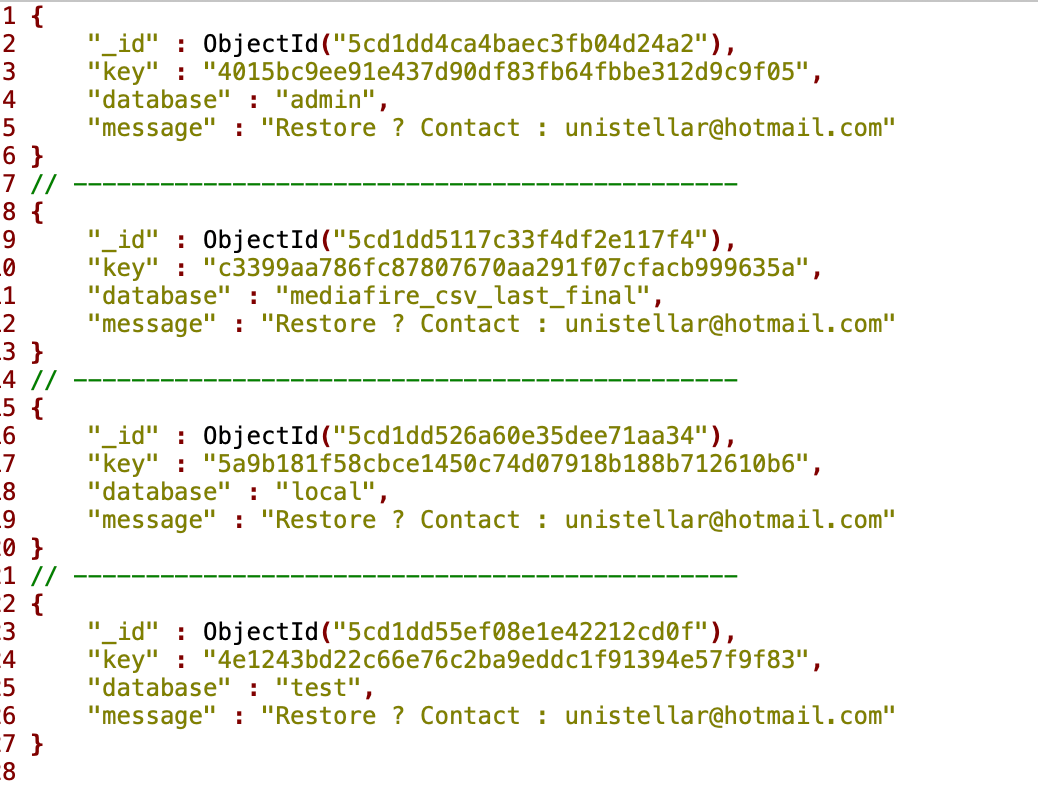
Message left by hacker group ‘Unistellar’. Source: Security Discovery
“While the actual number of exposed persons might be less than the total number of records exposed, it is still one of the biggest breaches reported in the region,” said Diachenko.
“Absence of the affiliation don’t [sic] make this incident low-profile.”
The significance of these data leaks is in highlighting how MongoDB databases are being left unsecured by their owners. Aside from the ethical issues of PII in the open, it also means malicious actors could block access to data by securing a database.
Arising in the mid-2000s under the NoSQL banner, MongoDB is used for big data applications and other processing jobs involving data that doesn’t fit well in a rigid relational model. Instead of using tables and rows, MongoDB uses a non-relational, document-oriented database model which supports various data forms.
YOU MIGHT LIKE

Struggling to find data talent? Look beyond Ivy League
Jonny Milliken, manager of the research team at cybersecurity company Alert Logic, said the data leak demonstrated the importance of companies taking responsibility for their part in the “shared security model” when using cloud services.
“There is a huge volume of similar instances of this happening right now, accessible over the internet,” said Milliken. “Anyone who runs MongoDB in the cloud should take this as a warning […]”
According to Bleeping Computer, Diachenko was also behind the discovery of multiple other unsecured databases and servers.
In March this year, he discovered a database containing over 808 million email records, and another with more than 200 million records from Chinese job seekers at the start of the year.
The damage of exposing this PII for consumers shouldn’t be underestimated, said Ryan Wilk, Vice President at NuData Security, a Mastercard company.
“PII, combined with other user data from other breaches and social media, builds a complete profile.
“In the hands of bad actors, these valuable identity sets are usually sold to other cybercriminals and used for myriad criminal activities, both on the Internet and in the physical world,” Wilk said.
“Using these real identities, and sometimes fake identities with valid credentials, they’ll take over accounts, apply for loans, and much more.”
It’s worth mentioning that MongoDB details how to properly secure its databases on its documentation website, and features a security checklist for administrators using the platform.









