Phishing ‘main attack vector’ for industrial enterprises
Phishing emails with malicious attachments are the main attack vector for penetrating industrial enterprises, according to a report by Kaspersky, which says the type of attack has become “route for workstations in the industrial sphere.”
The phishing emails are “carefully crafted”, and appear to be sent from real companies masked as business correspondence, including commercial offers, invitations to tender, or requests for payment. Certain attacks have even used legitimate documents, which have been stolen in preparation.
“As a rule, stealing money is the ultimate goal of phishing attacks on industrial enterprises,” read the report.
“However, it is impossible to be sure that some of these mass attacks are not targeted attacks disguised as ‘standard’ industrial phishing.”
Kaspersky says that malware attached to phishing emails is a threat not only to workstations on the corporate network but to some of the computers in the industrial infrastructure. The Russian cybersecurity firm claims that spyware, backdoors, and keyloggers have been detected on at least 4.3 percent of ICS computers in the world.
“As phishers actively implement their attacks on industrial enterprises using malicious email attachments, we have seen the percentage of ICS computers attacked via email clients grow,” Kaspersky said.
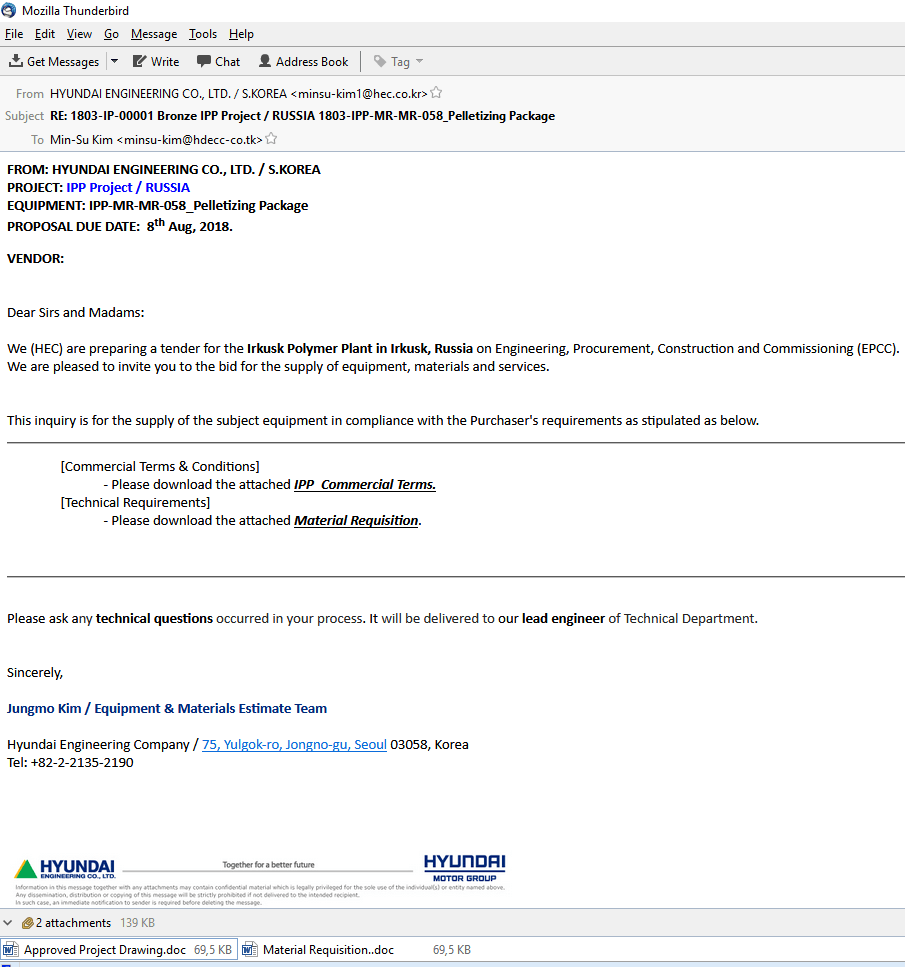
Phishing email. Source: Kaspersky

Phishing email. Source: Kaspersky
When it comes to which sectors are the most vulnerable to exploitation, Kaspersky said the largest number of vulnerabilities are within ICS that control critical manufacturing across various industries, in the energy sector and water supply. Others rated vulnerable included food processing and agriculture, as well as the chemical industry.
Meanwhile, the most common types of vulnerabilities include buffer overflow (Stack-Based Buffer Overflow, Heap-Based Buffer Overflow, Classic Buffer Overflow) and improper input validation (Improper Input Validation).
At the same time, 16 percent of all published vulnerabilities are authentication issues and access control issues, while 10 percent are web-related vulnerabilities (Injection, Path traversal, Cross-site request forgery (CSRF), Cross-site scripting, XXE).
Kaspersky says that 46 percent of the vulnerabilities identified, if exploited, could lead to remote code execution on the target system or a denial-of-service (DoS) attack. A significant part of the vulnerabilities (21 percent) could also enable an attacker to bypass authentication.
YOU MIGHT LIKE

Cyber attacks on non-standard ports tripled in 2018
In addition, special care should be taken with vulnerabilities in various industrial applications used by engineers and operators to access ICS via smartphones and tablets running Android or iOS.
“Such mobile applications are increasingly used in the ICS infrastructure. However, their security level leaves much to be desired, which is fraught with significant risks: compromised mobile applications can cause the entire ICS infrastructure to be compromised.”
An escalating risk
A key finding in the report was that almost half the world’s Industrial Control Systems (ICS) were subject to malicious cyber activity last year, with the group warning about the scaling risk to ICS computers around the world.
The findings are particularly poignant following the ransomware attack of multinational Norwegian manufacturer Hydro, which has so far cost damage of the attack at approximately US$40 million.
Kaspersky’s own customers were the subject of its research, where it found that the number of affected systems rose from 44 percent in 2017 to 47.2 percent in 2018. According to the firm’s report, the hardest hit countries were Vietnam (70.1 percent) and Algeria (69.9 percent).
In contrast, Ireland (11.7 percent), Switzerland (14.9 percent) and Denmark (15.2 percent) are some of those currently at less risk.
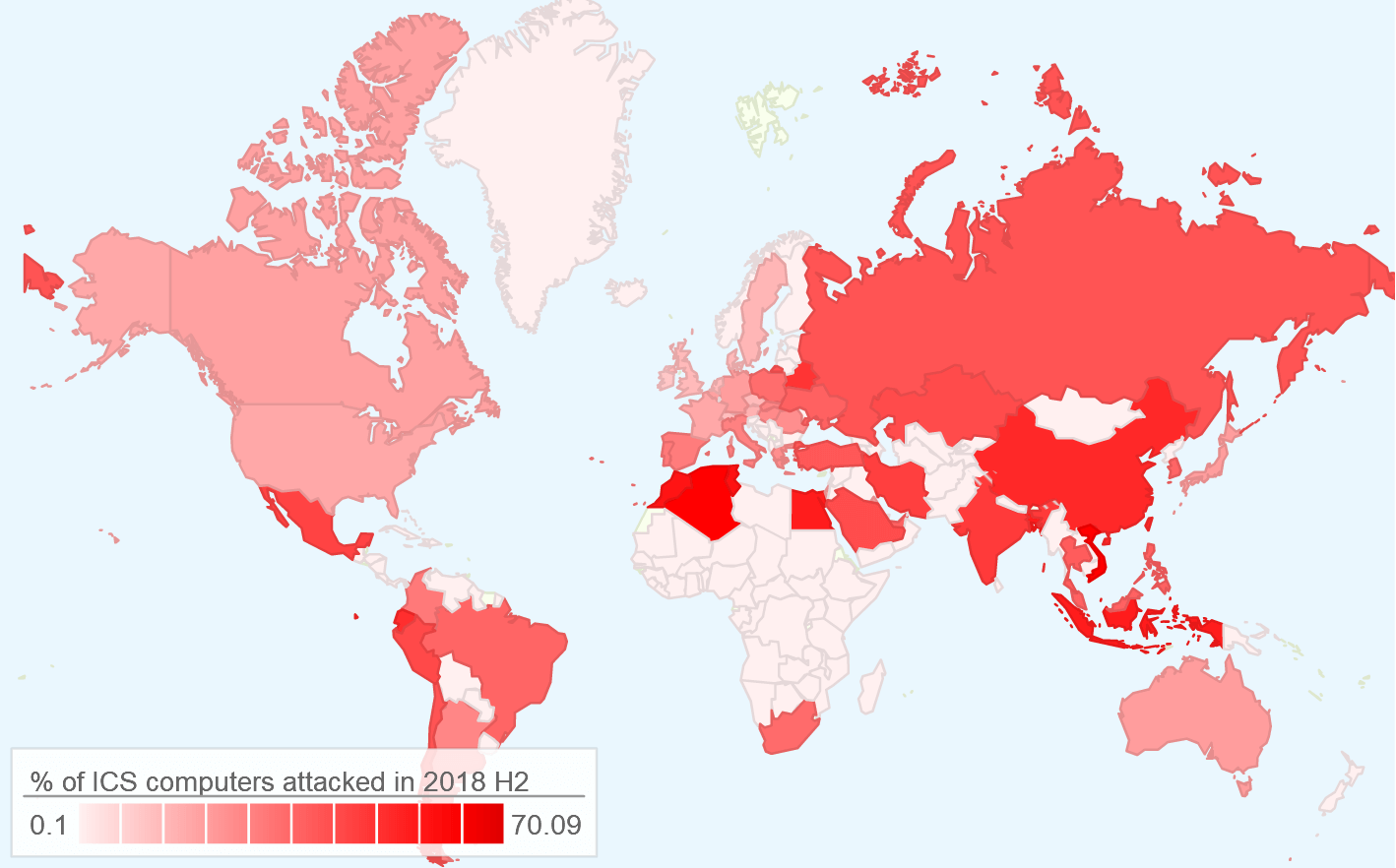
Geographical distribution of ICS attacks in 2018. Source: Kaspersky
Kaspersky Lab’s security researcher, Kirill Kruglov, explained that the main source of threat to industrial computers is not thought to be targeted attacks. However, it’s not to say mass-distributed malware can’t or won’t access ICS accidentally or otherwise via phishing emails, or even removable hardware such as USB sticks.
Causing production downtime and material losses, ICS attacks can be incredibly damaging. In the case of Hydro, for example, the group which employs 40,000 staff in 40 countries were forced to switch its smelting facilities to manual operations for an extensive period.
Going back to 2015, meanwhile, a hack of Ukraine’s power grid caused a blackout affecting 200,000 people.










