Banking trojans top email threats as Ransomware wanes
Cybersecurity is a complex yet pressing issue for any organization with an online presence and in 2018, the sheer magnitude of attacks on organizations made for another sobering reality check.
A new report from cybersecurity specialist Proofpoint highlighted the dominance of banking trojans, which accounted for 56 percent of all malicious email payloads in Q4 last year. These comprise malicious computer programs designed to gain access to confidential information stored or processed through online banking systems.
Once installed, a banking trojan can gain access to computer files and systems— the program is built with a ‘backdoor’, allowing outside parties to gain access to the device.
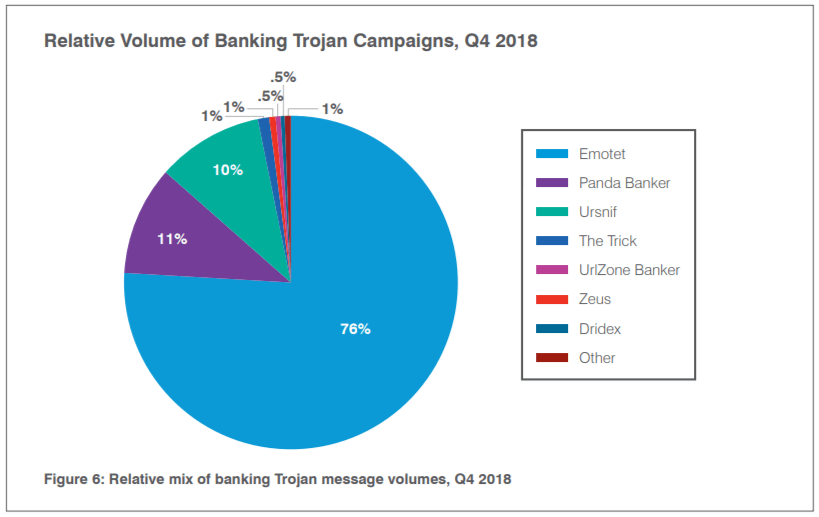
According to the report, despite the presence of a range of banking trojans appearing ‘in the wild’, threat actors continue to coalesce around known malware; Emotet accounted for more than three-quarters of occurrences, alongside other recognized malware types Panda Banker and Ursnif.
Source: Sourcepoint
As email fraud continued “dramatic” growth, rising 476 percent year-on-year for the period, Remote Access Trojans (or ‘RATs’) representing malware programs that include a backdoor for administrative control of a computer— accounted for 8.4 percent of email-borne attacks.
YOU MIGHT LIKE

What can we learn from Visma’s cybersecurity breach?
RATs are initially used to start downloads for other tools, but once they are in the system, hackers can remove all valuable data while keeping host users in the dark. Tools employed are increasingly versatile, allowing threat actors to deliver secondary payloads, deploy cryptominers and collect a range of user data.
“Threat actors follow the money, meaning that they would not be increasing distribution of RATs without achieving a return on their investments in malware, command, control, and sending infrastructure,” read the report.
During the research, Proofpoint discovered that Ransomware was “virtually absent” from its research, comprising just one-tenth of 1 percent of overall malicious message volume— a result of them not generating enough return to be distributed at scale.
As Ransomware waned, however, a new threat became more commonplace— ‘direct extortion’. These campaigns may take the form of ‘sextortion’ or other forms of blackmail in which threat actors threaten to reveal compromising information or take destructive action if the victim does not pay a fee.
With “rare exceptions” do these email attacks contain malware or malicious links, instead relying on the human factor to trick recipients, although emails will often contain ‘evidence’ of compromise such as an old password that the actor may have obtained from a data breach.
“Regardless of the particular scenario, it appears that threat actors have discovered that it is easier and less expensive to attempt to extort payments directly from victims rather than to distribute ransomware,” said Proofpoint.
All in all, 60 percent of companies saw their own domains spoofed by email fraud actors, an increase of almost 10 percent from the previous quarter.
The report also flagged the rise of web-based attacks, which include social engineering schemes and embedded cryptocurrency mining on the web.
YOU MIGHT LIKE
10 worrisome ransomware predictions for 2019
Social engineering attacks represent a pervasive threat and present web surfers with fake antivirus notifications and software updates that lead to malware downloads, phishing landing pages and more.
Finally, social media channels remain “key vectors” for fraud and theft. Despite the platforms themselves developing automated protection, social media support fraud remains a key challenge for consumers and the brand they interact with.
Known as ‘angler phishing’, these attacks see threat actors inserting themselves into legitimate interactions between consumers and brands and saw an increase of 40 percent from the previous quarter. Over the course of 2018, angler phishing accounts have increased by over 500 percent.









