Connecting apps to a SaaS stack is almost second nature to some people. Users extend Google Docs form-building capabilities with tools like Automagical Forms, import images with Pixabay Free Images, and ensure text is original with PlagiarismCheck.org. It’s done in a moment, without a second thought to any security considerations.
In its latest report, Uncovering the Risks & Realities of Third-Party Connected Apps, Adaptive Shield takes a deep dive into these third-party apps. Using aggregated, anonymized customer data from over 200 tenants, the report helps security teams get a deeper understanding of both the breadth and depth of this issue.
The report looks to answer three key questions.
- How many third-party apps are connected to a company’s SaaS stack?
- What types of permissions are these apps asking for?
- How real is the risk that connected apps pose?
Lots of Connectivity
There are two primary factors that drive app usage – the number of SaaS users and whether your company uses Microsoft 365 or Google Workplace.
Regardless of the platform being used, the number of apps increased with the number of SaaS users. Companies using Microsoft 365 with 10,000 SaaS users averaged 2,033 third-party apps; companies of the same size using Google averaged 6,710 apps. Those numbers changed considerably based on the number of SaaS users in a company.
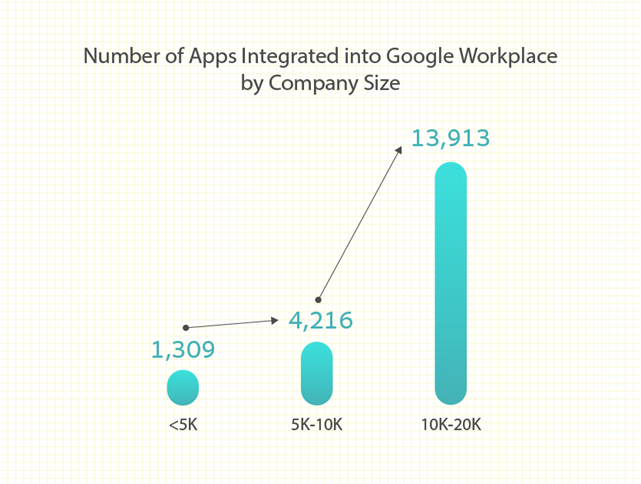
Figure 1. Average number of apps integrated with Google Workspace by users. Source: Adaptive Shield
Users grant significant permissions
The report divides the risk level of app scopes into three categories: low, medium, and high. For Google Workspace apps, the categorization followed Google’s definition of Sensitive and Restricted scopes for medium and high, and those standards were applied to apps in the Microsoft ecosystem.
Nearly 80% of all apps that connect to Google Workspace were considered medium risk level. Low risk apps made up 11% of connected apps, as did high-risk applications.
Apps connecting to Microsoft were significantly higher risk, meaning they requested far greater invasive permission sets than apps requested from Google. In contrast to Google, 39% of apps connected to Microsoft requested high-risk scopes. 28% were medium, and 33% were low.
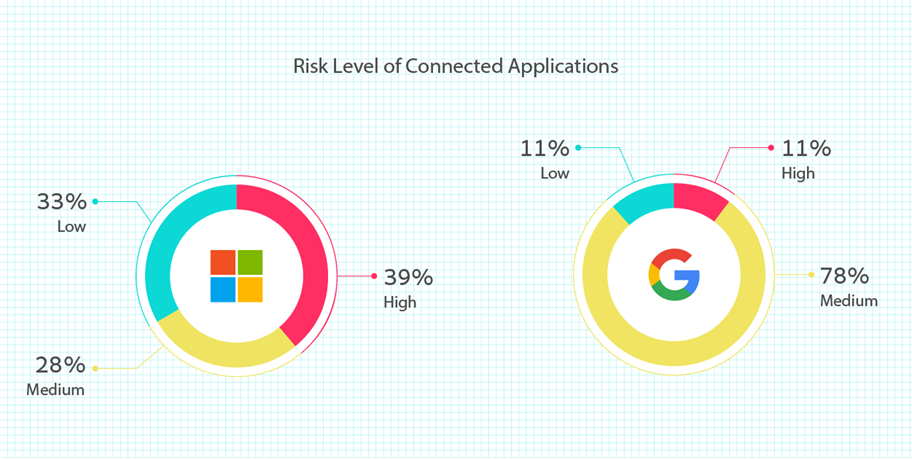
Figure 2. Risk level for apps connected to M365 and Google Workspace. Source: Adaptive Shield
What can SaaS-to-SaaS apps do?
Based on the permission scopes granted, a large number of applications have a wide berth. In Microsoft, 27% of applications with high scopes are able to read, update, create, and delete content. Apps are granted full access to mailboxes, and can send email as the user.
Google Workspace’s high-risk app permissions are equally troubling. 78% of the high-risk scopes give the app permission to see, edit, create, and delete any or all Google Drive files, emails, and documents.
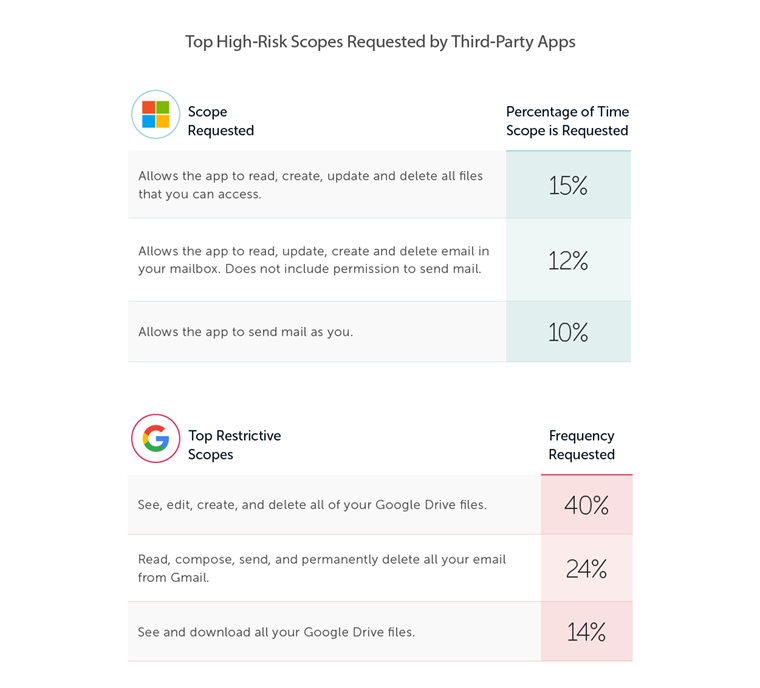
Figure 3. Top high-risk permissions requested by apps connected to M365 and Google Workspace. Source: Adaptive Shield
Those permissions pose a significant risk to company data, as apps can be taken over by threat actors, who can steal, encrypt, or publish the data that they find.
Takeaways from the report
Reading through the data, it’s clear that security teams need to improve their visibility into connected SaaS applications. Thousands of connected apps pose a risk to business-critical data, much of which is beyond the view of the security team.
SaaS security solutions, like Adaptive Shield, provide security teams with their best hope in securing this attack surface. It provides full visibility into the apps that are connected to the applications, as well as the permission scopes granted to the apps. With this data, security teams can make informed decisions for each application, and maintain the integrity and security of their data.
Download your free copy of the SaaS-to-SaaS Access report and see what’s hiding in your SaaS.









