Why protecting your emails means protecting your entire business
Prejudiced Perception of Cyber-Criminals
An enduring stereotype of cyber-criminals is of lone actors attempting to crack the FBI’s defenses with indecipherable, genius-level code, with political revolution or intellectual satisfaction at the core of their motivations.
Yet the truth is far more prosaic and entrepreneurial; the aim of most malicious actors is simply to earn money. Many cyber-crime gangs operate according to successful business models, requiring collaboration and sophisticated strategies. Each member of their team has a specific skill-set, all honed to maximize the chances of a successful breach. With some hacking organizations going so far as having customer support services and vendor review systems, the world of cyber-crime is not only lucrative but highly professional.
Premised on having as high a profit margin as possible, cyber-attack methodology is based on targeting the easiest threat vectors at scale, ensuring the largest pay-out relative to effort. As such, it is not perimeter defenses of the FBI, but inboxes of corporations that are the most vulnerable to today’s cyber-threats.
Exploiting the Email Vector
Exploitation of the email environment is nothing new. Since electronic mail became ubiquitous, spamming entered common parlance — and such drive-by attacks remain the easiest way of breaching an organization’s network. Almost 94 percent of attacks penetrate via the inbox. As many cyber-security experts will attest, it’s personalized, targeted phishing via email that remains the biggest threat to an organization, irrespective of industry sector.
When first invented, spam was combatted by relatively simple filters. Developed to catch relatively basic ‘click here to win a Mercedes-Benz’ communications, cyber-criminals soon learned how to circumvent these defenses with more sophisticated email campaigns. In response, cyber-security solutions evolved, and so the game of cat-and-mouse between companies and cyber-criminals continued. But, with malicious emails now consistently slipping through perimeter defenses, the traditional legacy approach has become insufficient against evolving attack strategies. If organizations want to stay ahead, they must adapt — the cyber-crime world certainly has.
Introducing The Evolved Criminal
With cyber evolution, malicious phishing attempts have started to consist of highly targeted messages, predicated on manipulating recipients to the utmost. By purporting to be from a co-worker, friend, or boss, these emails leverage victims’ tendency to trust against them — fooling them into believing the digital communication is from a legitimate source. Achieved by not only creating a credible spoofing address but more insidiously, piggy-backing onto existing communication threads, it is increasingly difficult to differentiate real communication from fake.
All this is made possible by malicious tools that are readily available for any purpose; malware-as-a-service is a fully-fledged business, and code which imitates language and style is now available.
With offensive AI beginning to be added to the mix, it will soon be ‘game over’ for organizations, unless they adapt to the new conditions of cyber-attack. Phishing emails’ calls to action will no longer be ‘please see attached,’ but ‘please review Anne’s latest edits to the new business proposal (final deadline Friday)’ — everything will be highly contextualized. Meanwhile, instead of a human achieving this effect after hours of research and planning, AI-powered tools will do the same in minutes.
A Digital Immune System
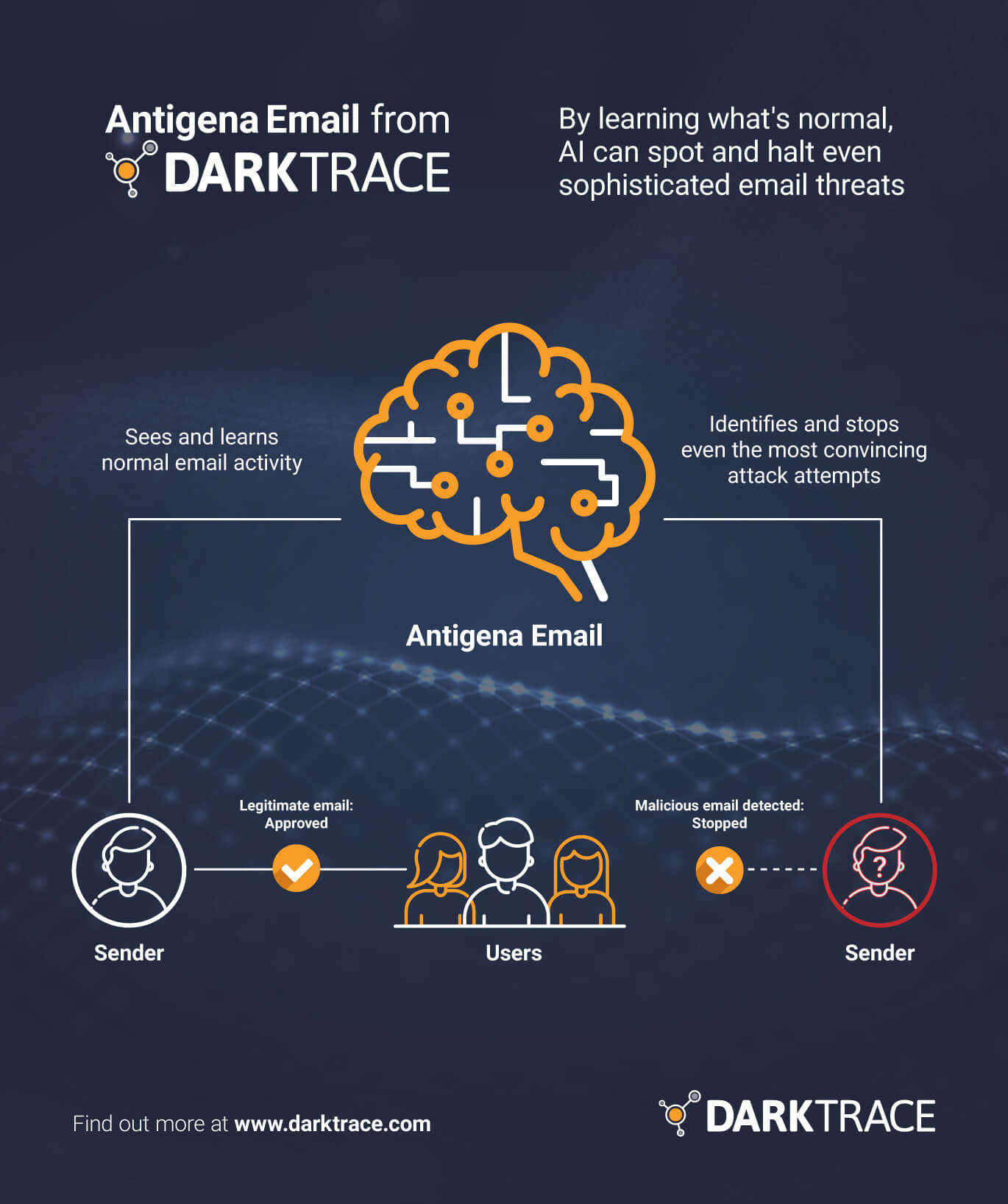
Current security postures’ fundamental problem is their treatment of each email as a static entity, rather than as a dynamic part of an employee’s digital life. To combat this, an immune system approach is necessary. Here, cyber AI technology learns what ‘normal’ looks like for every user, device, and connection on an organization’s network. Not only does this facilitate a greater understanding of companies’ environments, but places each piece of digital communication into context with an employee’s other digital activity — this understanding of ‘self’ enables instant detection of threats as and when they arise, no matter how subtle the indicators.
Darktrace, the world’s first provider of cyber AI, has already deployed such immune system technology at scale in organizations around the world. It combines its detection of ‘non-self’ with autonomous response capabilities that act as digital antibodies, responding and neutralizing threats seconds after they emerge. These capabilities were recently demonstrated by Darktrace’s autonomous response module for the email environment, Antigena Email. Here, the cyber AI technology detected a phishing attack targeting five high-profile users in an academic organization. Constructed to trick them into downloading a malicious payload, the email was supposedly from WeTransfer, a file transfer service, and would have appeared to be perfectly normal to the recipient — even the header data, ‘width’ and ‘depth’ of the email were consistent with previous communication. However, the IP address had a high anomaly score, as did the link in the email. Darktrace took autonomous action, holding back these emails and preventing delivery.
Antigena Email achieves such results by learning an organization’s DNA. Surgical response to threats in real-time is made possible by the holistic understanding of an employee’s cloud, SaaS, traditional network, operational technology, and email environment. And Antigena Email operates throughout an email’s lifecycle — from its delivery, opening, and reply, the technology is poised to intervene and protect a company’s digital estate. It can autonomously hold back suspicious emails for investigation, convert attachments into harmless PDFs, lock embedded links, and even spot data exfiltration via the outbox.
With Darktrace, threats are neutralized in seconds, and incidents are prevented from escalating into crises. Only a machine-speed response using defensive AI will be able to protect organizations from the escalating threat landscape cyber-criminals are creating.
To learn more about Darktrace’s autonomous response, and the rest of this breakthrough cyber-security platform, read more here.