Continuing but under increasing pressure – cybersecurity professionals’ attitudes, 2019
Find any article on cybersecurity in the mainstream press, on paper or online, and the accompanying picture will be of a lone figure, hooded, crouched over a keyboard. Creative picture editors may have added a backdrop of code usually comprising an innocent piece of CSS or JavaScript. While the article may intelligently discuss cybersecurity issues, the overriding impression given by the imagery is that hackers are lone wolves, running small extortion rackets.
What any security specialist will tell you, however, is that most bad actors (malware propagators, black hats, hackers et al.) are a part of well-organized, well-funded groups that act more like successful enterprises than loose collectives of ill-organized activists. With an overriding motive of creating profit, keeping costs low and driving efficient work practices (like any other business), hacking groups use the very latest in methods, technology and coding practice to select and exploit their carefully-chosen targets, before moving rapidly on to the next.
That degree of professional organization is one of the sources of stress that cybersecurity professionals face, according to an academic report run by Goldsmith’s College, University of London. From a survey of over 3,000 mid- to high-level IT professionals from the UK, France, and Germany, the report’s findings are an insight into the issues that worry and excite cyber protection and defense staff.
Apart from the levels of professionalism and organization that bad actors now exhibit (although the lone wolf does no doubt exist), cybersecurity managers also list regulations concerning data protection as among the issues that make their jobs stressful. Adherence to GDPR and proving the organization’s adherence to that raft of measures and similar instances, take up chunks of time, right when there aren’t enough hours in the day.
Cybersecurity staff are also finding a source of pressure from a widening skills gap, too. The existing workforce has, to a certain extent, been left behind by the change in many businesses’ IT deployments, with a shift to cloud and mobile topologies not adequately reflected in skill sets. In that, employers are perhaps to blame – lack of training may be the issue here, but whatever the case, a skill shortage indubitably exists; demand for skilled cybersecurity staff is outstripping supply. Many organizations might be minded to turn to a third-party service-provider to help relieve the strain, but multiple security systems and products make it difficult to hand over, wholesale, the raft of protective measures.
The growing complexity and speed of change in today’s IT environments are quoted by the survey respondents, too, whether that’s through the acquisition of new businesses or the easy availability of cloud storage and services: the shifting nature of the structures to be protected makes for a series of cybersecurity headaches.
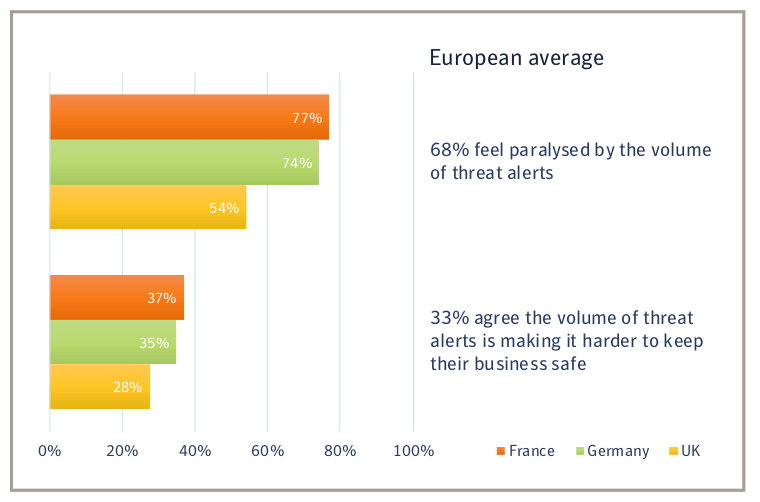
Source: Goldsmiths College
As new technologies have come online, cybersecurity systems have also sprung up to support and protect them. As a result, many IT functions are inundated with data, red flags, alerts, security briefing updates, and possible anomaly notices. Logfile processing systems vie with remote WAF notifications, in-house router and firewall alerts, desktop anti-malware notices – plus in many cases, reports and warnings from third parties – with the totality generally making for a stressful informational overload.
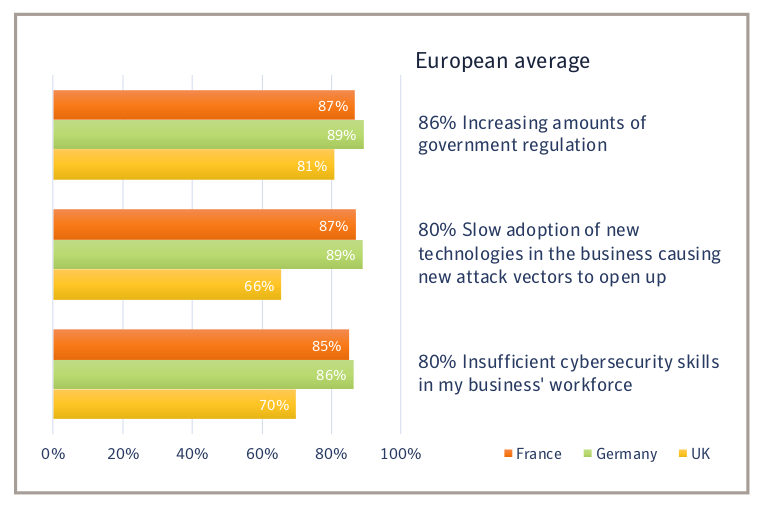
Source: Goldsmiths College
In the face of statistics proving trends like those mentioned so far, it’s refreshing to note that despite many cybersecurity colleagues thinking, on occasion, about leaving the field of data security altogether, most of the people surveyed (92 percent) said they were thrilled by their work, and 90 percent are motivated by high-pressure situations. In short, it’s an interesting field in which to work, but a demanding & stressful one, too.
But like any professional in any field, it’s the repetitive, the administration and the obstacles placed in the way, that make a working life unpleasant. While the arena of cyber defense is an exciting one, it’s the struggle with multiple platforms, different third-party suppliers and systems, and a lack of a single, trouble-free framework from which to work that bothers many.
No-one would expect a Finance Director to work from three or four versions of Excel, a couple of instances of Quickbooks, and now and then, to have to turn to in-house and cloud-based SAP installations to get their work done. But that’s precisely the type of situation that the quickly-moving cybersecurity environment is forcing on many professionals.
Keeping all the plates spinning is mandatory for the IT security function these days, but the truth is, it isn’t a solution that spells long-term safety and stability for the business; at least, not one that will leave cyber defense staff in the best of mental health! You can read about the pressures under which cybersecurity functions are under in the full report, available here (PDF).
Thankfully, there are a few platforms out there that are properly open, extensible, and powerful enough to act as a uniting force that encompass all the different capabilities that cybersecurity personnel need. We propose that an answer like the Symantec Integrated Cyber Defense approach would be a good investment: it’s one way that data security, adherence to governance like the NIS Directive and a more strategic role for the department can be achieved.
Rather than staff having to switch from one point product to another as red flags get raised, ICD integrates with the security elements already active in a security stack (Splunk, ServiceNow and so on), and other products too, like those from Fortinet & McAfee. The platform helps prioritize and organize what are effectively separate silos of information, each currently competing for attention. A proactive and holistic system, it doesn’t claim to be a golden bullet that ends cybersec concerns. Instead, it and the Symantec team will work with your cybersecurity specialists, platforms and partners to complement and ultimately transform your existing security infrastructure at a pace that suits. Get in touch with a Symantec representative to learn more.









