Privileged people and powerful systems: balancing trust with Thycotic
A phone call comes through to the IT Helpdesk at 6:20 pm on a Friday afternoon. The sole remaining technician takes the call. It’s a frustrated manager in the Finance Department who can’t access several documents on the company’s shared file store (lack of ‘sufficient privileges’), and her boss needs some figures before the weekend. The manager and IT technician alike are already looking at the exit with some longing, so to get the manager access, the tech elevates her account’s status so she gets the information she needs. Job done, and happy weekend!
That type of well-meaning action – or a variation on it – is repeated in businesses across the globe every day. In terms of cybersecurity, however, each is a potentially disastrous situation, and one that Thycotic is helping to solve. The security company’s ethos is to help to shore up the gaping hole that exists in most information security provisions in many businesses today; that of human error. In the case of our example above, privileged access to a company’s systems effectively grants the keys to the kingdom, and while that’s not a problem for those that understand the ramifications and require high-level oversight, in many cases, it’s a potentially serious situation.
In companies that number employees in the hundreds or thousands, managing individual access to resources digitally is almost impossible to do safely without centralized oversight and control, and it’s here that the Thycotic portfolio comes into play. Its offerings are based on two concepts: the first is that of least privilege, the second is of PAM, or Privileged Access Management.
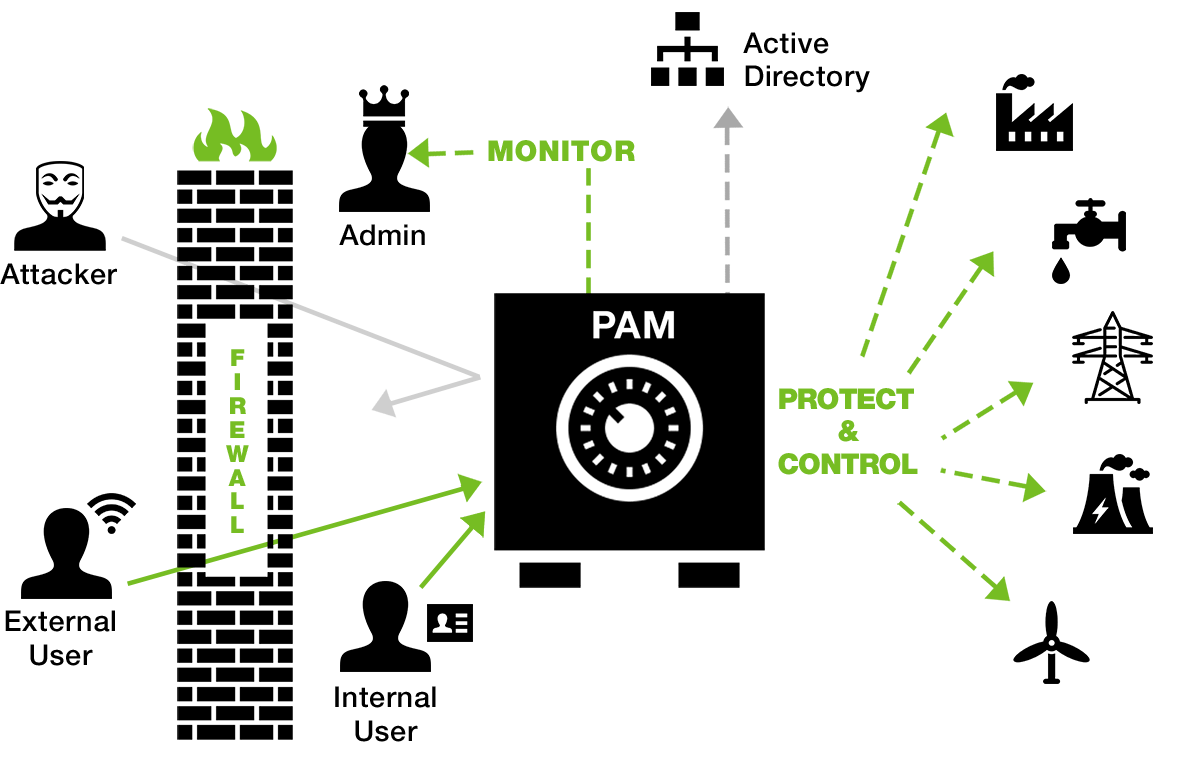
Thycotic Secret Server delivers an end-to-end, automated Privileged Account Management protection that provides an additional layer of security to help control, monitor and secure critical energy and utility infrastructure.
Anywhere in a business, in remote and home offices, distant warehouses, or the Wi-Fi network in the lobby of the head office, every device, application, and user that has too much privilege is an opening for an attack. To secure the corporate sieve, companies need to enforce least privilege, giving devices, applications, and users the absolute minimum privileges needed to do their jobs. But when privilege is removed unilaterally, without a way to securely provide privilege on demand, companies find themselves in the situation of our financial manager. In these cases, excessive privileges are all too often granted hastily, without auditing, controls, or assurance that those privileges will be quickly removed.
With the Thycotic suite, privilege is protected, while maintaining productivity through automated access rules. That means specific access could always be refused, only allowed to a carefully demarcated segment of the network or type of user, or be subject to validation by meeting additional security controls before access is approved or denied. Individual applications running on devices also have limited trust until recognized by Thycotic’s Privilege Manager, and at all times, apps, users and devices are only ever given access as high up as they need to go.
The further complication in managing all this is of course that requirements and access levels change over time. Every security professional (and harassed IT technician at 6:20 pm) will tell you that maintaining security on a per-application or per-device level is always a balancing act between what’s necessary in terms of access, and what’s advisable from a security perspective. But with Thycotic’s Privilege Manager, for instance, the process of establishing the correct levels of access in real-time becomes much simpler and more effective in reducing business risks.

The platform will discover all apps on all devices on the network, noting administrator or root level accounts, and place a policy-driven management framework over all endpoints, their users and the applications & services running on each. Privileges can be elevated on an application basis instead of a user basis so, for instance, an application may need access to a secure store, but the user should not be able to browse its contents. With Thycotic, that type of granularity is possible.
Unknown apps can be sandboxed, white/grey or blacklisted, and any unusual activity (atypical access to specific applications or systems, unusual log-in patterns, and so on) is flagged according to preset rules and tolerances. With Thycotic’s PAM solutions, another delicate balance is achieved, that of avoiding hundreds of red flags per minute, yet seeing alerts when anomalies happen.
On a more practical level, RBAC policy implementation (role-based access control) can be delegated (to department managers, for example), and there’s integration with existing systems (or override of) Active Directory, LDAP, SSO or local UAC. Oversight includes configurable logging, SIEM integration, and dashboard-based management and control, plus as you might expect, password policies like rotation, expiration and the blocking of unsafe choices are standard.
From initial discovery of user credentials, application, and endpoint audit, through to continuous monitoring and adjustments, long-term monitoring and security, the Thycotic platform offers businesses a way around the element of human mistakes that causes data breach and loss of intellectual property.
The framework is available for in-house implementation, or as a cloud service. As a PAMaaS (privileged account management as a service), organizations can get up and running in record time, carefully bedding in new policies to ensure that systems work more safely and achieve the delicate balance between limiting their users’ ability to work and granting too much (potentially dangerous) freedom.
To learn more about Thycotic’s powerful and technologically-advanced PAM solutions aimed at the human and silicon elements of your organization, get in touch today to try before you buy.









